2024 is therefore a pivotal year. ANSSI is preparing to unveil its roadmap and it is time for companies to ask themselves where they really stand in terms of quantum strategy. Because unlike the cloud, which has become established gradually, the adoption of quantum must be immediate for everyone in order to remain aligned with customer needs, but above all in order to protect ourselves from the risks of this revolution.
A revolution of unprecedented scale and speed
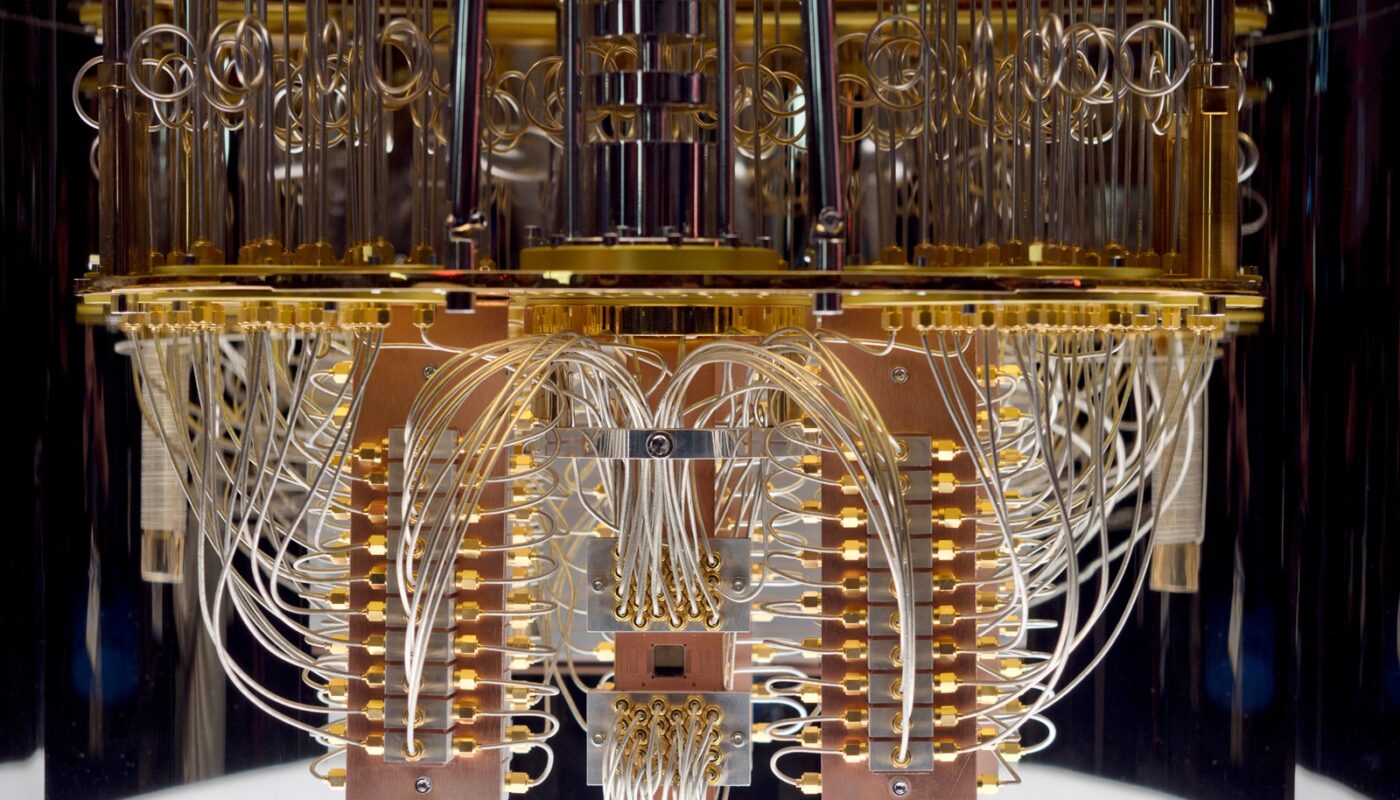
Principle of quantum computing: qbits and super calculations
By definition, quantum computing is a technology based on superposition. This makes it possible to transform a classic computer using a binary language into a machine more powerful than supercomputers. Based on the principles of quantum physics, thanks to which it is possible to study the infinitely small, this new computer is capable of solving in the space of a few seconds a calculation that could have taken a few hundred days on a traditional machine .
Concretely, during a search, a classic computer successively scans the bits, these multiple sequences of 0s and 1s, until it finds the result. For its part, the quantum computer will use the principle of superposition allowing particles to exist in several states at the same time: the traditional bit then becomes a qubit (quantum bit), it is no longer 1 or 0, and can be several combinations at once. During research on a quantum computer, it will therefore no longer be a question of scanning each sequence of 0s and 1s one after the other, but all at the same time, thus considerably speeding up the processing time.
The limits of quantum: first a hybrid platform, then quantum
If companies like IBM or Google announce the arrival of their respective quantum computers in 2035, their installation, strictly speaking, will not be immediate. Indeed, although they make it possible to study the infinitely small, quantum states are extremely fragile and manipulating a qubit requires using atoms whose temperature is close to absolute zero (-273°C) . Such an imperative therefore requires gigantic cooling tanks. It is therefore impossible to imagine installing this type of machine in current data centers which, for their part, generate heat. These constraints therefore force manufacturers to develop, initially, a hybrid technology combining quantum and traditional computing, and presenting itself as a logical evolution between traditional computing and quantum computing.
There is an urgent need to deploy these solutions since the national strategy on quantum technologies, presented in 2021 by President Emmanuel Macron, allows, among other things, the installation of a quantum computing platform in Saclay (Essonne). Combined with existing supercomputers, it offers users the opportunity to familiarize themselves with the power of quantum computing through emulators, while waiting for dedicated computers to become a reality for everyone. This therefore implies that companies must today bring together pre-quantum and post-quantum in their technologies in order to offer, on the one hand, an offer available for both traditional computing and quantum computing, but above all to anticipate new threats, and therefore review their defensive strategy.
Electronic signature versus quantum
NIST barrier algorithms: CRYSTALS-Kyber, CRYSTALS-Dilithium, FALCON and SPHINCS+
Quantum computing is overhauling computing as we know it today. With its unprecedented computing capabilities, it will destroy all current security concepts from the first second a quantum computer is connected to the Internet. At the same time, the world will automatically enter a post-quantum era.
Protect yourself from a new generation of attacks
Until now, public key cryptography, which makes it possible to secure email exchanges, protect financial transactions carried out online or develop secure e-signature services, was protected from threats. The quantum algorithm for factoring integers, known as Shor’s quantum algorithm, disrupts this tranquility since it allows the identification of prime factors of all numbers, whether integers or natural numbers, and the deciphering of these cryptographic systems.
On its own, this algorithm would therefore represent the greatest threat to quantum computing. By decrypting data, a malicious actor can, for example, intercept authentic signatures and reproduce them perfectly to pass them off as real and therefore legal. By doing this, it will then be possible to usurp the identity of a victim and carry out financial transactions in their name.
Faced with this prospect, the electronic signature market is forced to review its cybersecurity strategy. If technology today makes it possible to detect and protect against certain threats, it is quite the opposite with quantum, because of its power and its calculation speed. The same goes for electronic archiving systems whose integrity will be threatened by algorithms like Shor’s.
If the quantum computer is not yet a reality for everyone, authorities such as ANSSI recommend a hybrid use combining a post-quantum algorithm with other recognized and proven pre-quantum public key algorithms. While waiting for the ANSSI roadmap, it is imperative for companies to be ready by reviewing their cybersecurity strategy and completely rethinking it to include the quantum threat by recruiting dedicated teams. If the quantum threat will jeopardize their activity, it will also affect their customers and users.
With quantum, the saying ” Prevention is better than cure “ makes sense. It will be the revolution of the century, but it will also give rise to a new generation of formidable threats. Unlike technologies like the cloud or Artificial Intelligence, for which companies had the choice and, above all, the time to prepare, quantum will leave no escape. It is therefore urgent to act!